IeCeTee
Fortifier
One tool to rule them all!
We specialize in complex software systems that beat all current benchmarks to make sure you get the best security assessment that is available in today's market. We have written thousands lines of code, we have done extensive scientific research and we have spend thousands of hours creating a toolset to assess your environment in a revolutionary new way. I gladly introduce you to Fortifier: the first and last cyber security environment you will ever need.
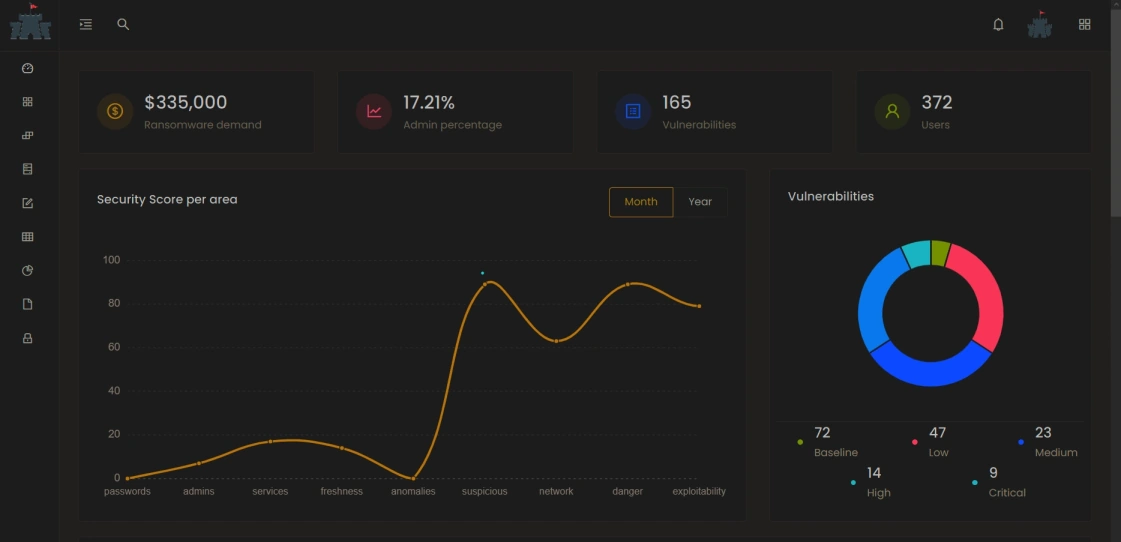
Vulnerabilities
Our environment was tested to find more vulnerabilities then any other.
Environment wide
We test wifi. websites, internal networks, (Azure) AD and Google workspace.
Enhancing security
Using FRIS, we are the first security assessment tool that includes solutions for found vulnerabilities
Artificial Intelligence
We use the power of artificial intelligence in reporting and explaining found vulnerabilities.
Our Systems
in numbers
For a security company, stats don't lie.
Lines of code
Unique vuln discovered
Github commits
Happy Employers
Fortifier explained
Our Story so far
Over time, Fortifier has advanced.
A short summary of our capabilities and features.
Fortifier for Active Directory
2022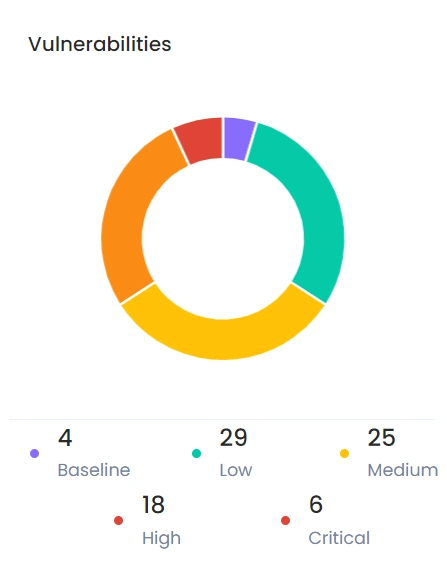
Stronghold AD pentests
We created a system called Stronghold to automatically assess Active Directory for vulnerabilities. Stronghold scans for CVE's, misconfigurations and even checks hashes of users with the haveibeenpwned hashlist to verify that passwords are stil considered secure.
We have compared Stronghold with the current state of the art in AD penetration testing, Purple Knight by Semperis and Pingcastle. We outscored both of them comfortably while also missing not a single vulnerability that our competitors found. Therefore we are very happy to present Stronghold as the new State of the Art in AD pentesting.
- STOTA vulnerability assessment
- Solve with ready powershell scripts
- Extensive reports of assessment.
Fortifier for Azure AD
2022/2023Stronghold Azure pentests
Stronghold works just as well for Azure Active Directory, it enumerates a set of handy conditional access policies and let you roll them out if missing. It checks compliance, bitlocker, mfa, legacy and also other things like update cycles or the presence of insecure windows distributions. We are the current State of the art for Azure vulnerability assessment.
Details +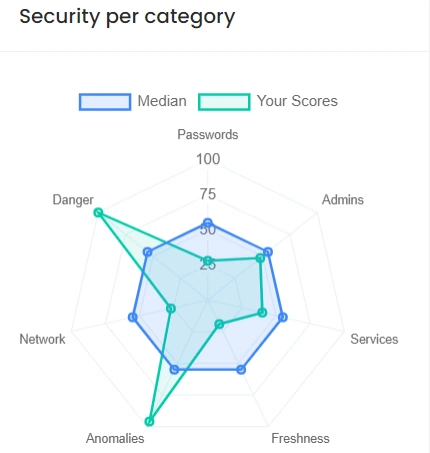
Fortifier for Google Workspace
2022-2023Stronghold Workspace pentests
We apply the same system to the worlds first automatic enumeration tool for google Workspace, we enumerate groups and settings to find misconfigurations and improperly setup groups/accounts. In similar fashion as to Azure, we check MFA, legacy and common issues:
- STOTA vulnerability assessment
- Solve by following written out steps.
- Extensive reports of assessment.
We generate extensive reports with impact analysis, steps to solve and steps to reproduce the issue, as well as links to official documentation or info about the found vulnebarility.
Fortifier for Phishing simulation
2022-2023
GateKnocker phishing simulation
GateKnocker is a novel phishing simulation tool. We test multiple phishing mails on your organisation, internal spoofed mails, external mails and mails from Google/Microsoft. We check what categories are vulnerable and we record which employees fall for the traps we lay out. We use our AT IT cycle to train your employees in multiple cycles and maximize their skillset of phishing recognition. We do this faster and better then known services while also offering 4 learning moments and 3 reports.
- 4-Fold repetition for maximum learning capicity.
- 3-Fold reporting for maximum insight of your environment.
- State of the art sophistication and phishing techniques.
Fortifier for Web Applications
2022-2023Besieger website pentesting
We have written Besieger, our tool for website penetration testing, we automatically check with a set of scanners given our custom IeCeTee templates, we also use dedicated systems to check for SQL injection and Cross Site Scripting. In addition to this we use some automated technology to identify the technologies used in your website and check all componenents for known exploits. We couple this with checks for standard passwords.
Fortifier for Internal Networks
2023
Keepbuster Internal network penetration
KeepBuster is our dedicated tool for internal networks. It enumerates the network, find services running on internal devices and seeks to exploit these with a list of attacks. It tests for a custom password list, default passwords and common passwords. In addition to this it checks for outdated software and components that have exploits available to them inside of the internal network. It's third attack is to find any misconfigurations present in the devices and services that are running inside your internal network. With internal networks being as messy and big as they often are, one single sub protocol or password can be enough to get deeper into the environment. This is why we recommend this kind of scans.
- Outdated protocol detection.
- Misconfiguration finder.
- Password spraying attacks.
Fortifier for Password security
2022-2023Armorer for Password security.
We have created armorer a tool that generates a password list based on personal and company information. This list, combined with the haveibeenpwned hashes list, is then used against passwords you type in. This means that we check if the password is present in any of these lists, if the password is, your hash would be already compromised or easily guessable and we therefore enforce you to use a password that is not. The application of this tool is to ensure that everybody across the corporate surface has a unique and strong password that is not easily hackable by hackers.
Fortifier in action
To show you the encapsulated environment we created with fortifier, we gladly present some footage of a report that was generated by using Fortifier in a Active Directory context. We also showcase our FRIS system.
Meet FortifierHow it's done
Our Working Process
In order to offer high quality services, our encapsulated work cycles are finetuned and maintained as follows:
-
Automate & Investigate
01.Cycle of automated penetration
We use automated penetration testing to test the entire environment for vulnerabilities lurking from all directions.
More Details -
Manual & Sophisticated
02.Cycle of manual penetration testing.
We do extensive manual penetration testing where we scan for more sophisticated and unique vulnerabilities.
More Details -
Report & Group
03.Cycle of inspection and perfection.
We create one big functional report with multiple small subreports of subenvironments, combining manual and automated labor.
More Details
Want to know more about what we have to offer?
Our servicesIecetee Innovation and
Development radar
Innovation and Development excite us and are an integral part of our company. We are always busy to improve and adjust fortifier. We do this on the pentest side by developing more and better vulnerability assessment tools but also on the reporting side where we create better and bigger reports with more information. We incorporate A.I in our research and try to always keep improving.
Artificial Intelligence
Incorporating A.I. into Fortifier for smarter pentestingReporting assistant
Pentest Language model
Reinforcement learning pentests
Software Development
Fortifier extensions that are planned.Additional surfaces
Additional penetration testing surfaces in developmentPhysical pentesting
Wifi pentests
Information finder
Fortifier subcomponents.
Learn more about all the different components that our Fortifier system encapsulates, see first hand what we have to offer accross different disciplines.
About FortifierPast projects
Some client Reviews
A recruiter once told me that a good recommendation can mean more then a thousand words.
So I took his advice and gathered a few.